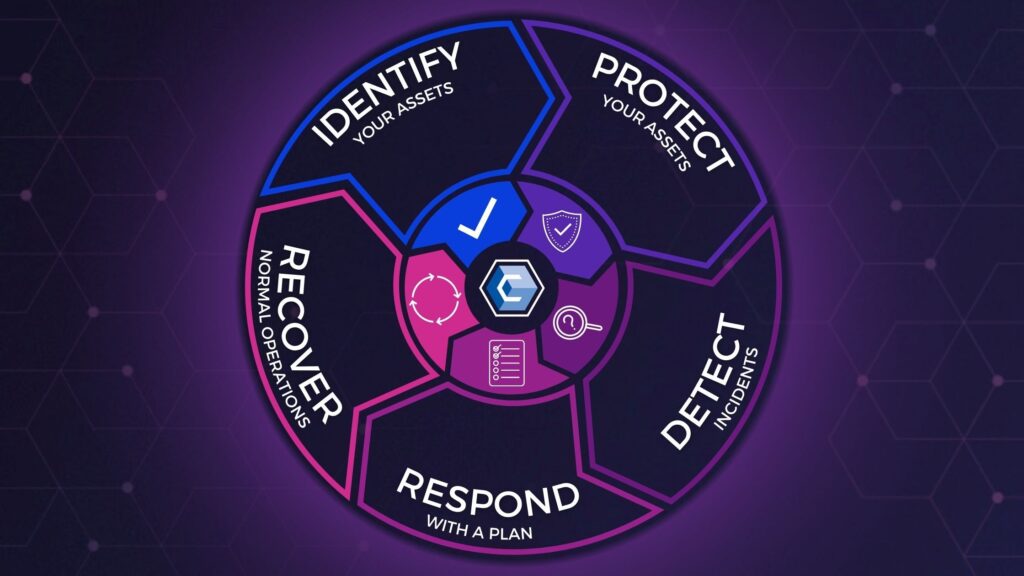
Cybersecurity refers to the practice of protecting computer systems, networks, devices, and data from unauthorized access, theft, damage, or other malicious attacks. It involves implementing various security measures to ensure the confidentiality, integrity, and availability of information and systems. Cybersecurity aims to prevent cyber threats such as hacking, viruses, phishing, ransomware, and other forms of cybercrime that can compromise sensitive information, disrupt services, and cause financial losses or reputational damage.
Where Did The Name CyberSecurity Come From?
The term cybersecurity is derived from two words – “cyber” and “security”. “Cyber” is a prefix used to describe anything related to computers, information technology, and virtual reality, while “security” refers to the protection of something from harm or danger. Therefore, cybersecurity refers to the protection of computer systems, networks, and devices from unauthorized access, theft, damage, and other cyber threats. The term “cybersecurity” is used to distinguish the protection of computer systems and networks from physical security measures that protect physical assets such as buildings and equipment.
What Was The First Recorded Cyber Attack
The first recorded cyber attack is believed to be the Morris Worm, which was unleashed on the internet on November 2, 1988, by a graduate student named Robert Tappan Morris. The worm infected thousands of computers and caused significant disruptions to the internet, highlighting the need for cybersecurity measures.
What Are The 10 Most Common Attacks
- Phishing attacks: A type of social engineering attack in which attackers use emails, text messages, or other communication methods to trick users into providing sensitive information.
- Malware: Short for malicious software, malware is software designed to cause harm to a computer system, network, or device. This includes viruses, Trojan horses, ransomware, and spyware.
- Distributed Denial of Service (DDoS) attacks: These attacks attempt to overwhelm a website or server with traffic in order to disrupt access for legitimate users.
- Password attacks: These attacks are attempts to gain unauthorized access to a system or network by cracking or guessing passwords.
- Man-in-the-middle attacks: This type of attack involves an attacker intercepting communications between two parties in order to eavesdrop or manipulate the conversation.
- SQL injection attacks: A type of attack in which an attacker exploits a vulnerability in a website or application to inject malicious code into a SQL database.
- Cross-site scripting (XSS) attacks: This type of attack involves injecting malicious code into a website in order to steal sensitive information from users.
- Zero-day exploits: These are attacks that exploit previously unknown vulnerabilities in software or systems.
- Advanced Persistent Threats (APTs): APTs are long-term targeted attacks aimed at stealing sensitive information or disrupting operations.
- Insider threats: These are threats posed by employees, contractors, or other trusted individuals who have access to sensitive information and use it for malicious purposes.
10 Resources To Help You Stay Up To Date With CyberSecurity
- ZDNet UK: ZDNet UK provides the latest news, analysis, and insight on the UK cybersecurity industry. It covers topics such as data breaches, cyber threats, and government cybersecurity policies.
- SC Media UK: SC Media UK provides in-depth news and analysis on the latest cybersecurity threats, vulnerabilities, and technologies. It also includes features on cybersecurity best practices, compliance, and risk management.
- The Register: The Register is a UK-based tech news website that covers the latest cybersecurity news, alongside other tech news. It often provides an irreverent take on the news, making it an entertaining read for tech and cybersecurity enthusiasts.
- ComputerWeekly: ComputerWeekly provides the latest news and analysis on UK cybersecurity, including data protection, privacy, and compliance. It also covers topics such as cloud security, identity and access management, and threat intelligence.
- Infosecurity Magazine: Infosecurity Magazine covers the latest news and analysis on the UK cybersecurity industry, including emerging threats and technologies. It also includes features on cybersecurity strategy, risk management, and compliance.
- Dark Reading: While not specifically focused on the UK, Dark Reading is a popular cybersecurity news website that covers the latest global cybersecurity news, including emerging threats, breaches, and technologies.
- Cyber Security Intelligence: Cyber Security Intelligence provides the latest news and analysis on the UK cybersecurity industry, including data breaches, malware attacks, and cybercrime trends. It also includes features on cybersecurity best practices and emerging technologies.
- IT Pro: IT Pro covers the latest news and analysis on UK cybersecurity, alongside other tech news. It includes features on cybersecurity strategy, risk management, and compliance, as well as practical advice for IT professionals.
- Cybersecurity Ventures: Cybersecurity Ventures is a research and advisory firm that covers the latest cybersecurity news, trends, and technologies globally. While not specific to the UK, its analysis and insights provide a valuable perspective on the global cybersecurity industry.
- The Daily Swig: The Daily Swig provides the latest news and analysis on UK cybersecurity, including emerging threats, vulnerabilities, and technologies. It also covers topics such as data protection, privacy, and compliance, and includes practical advice for businesses and individuals.

